By Jane Ginn
Final comments on the Framework developed by the National Institute for Standards and Technology (NIST) in response to E.O. 13636 on cyber security will be due December 13. While many commentators are focusing on how to incentivize private companies to participate in the voluntary program, my main concern focuses on the technical basis for information sharing. This essay presents a short history on the development of information sharing frameworks. In my next essay I will detail the main concerns and considerations private sector companies express when asked to divulge highly confidential cyber security related information that may threaten their intellectual property and customer databases.
Information Sharing Frameworks: A Short History
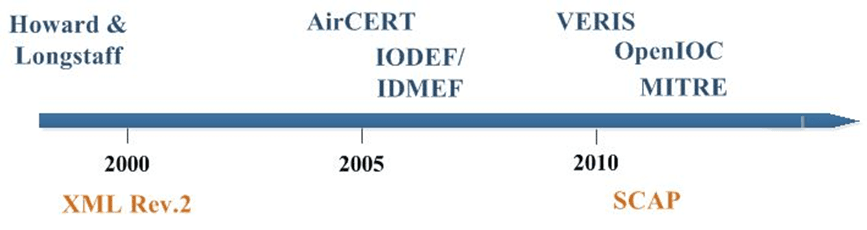
Beginning in about 1998 two researchers realized that computer security incident response teams (CSIRTs) within organizations could be more effective if they could share information between themselves. This need has become even more pronounced as the attack landscape has become more complex. Figure 1 displays the timeline for the development of the six frameworks that will be covered in this essay. Note that under the indicators of year markers there are two key events that also have bearing on information sharing, shown in orange font: 1) the issuance of the eXtensible Mark-up Language (XML) standard by the World Wide Web (W3C) consortium (Hollenbeck, 2003, January); and the issuance of the NIST framework for Security Content Automation Protocol (SCAP) (NIST, 2011).
Figure 1. Timeline for Key Protocol and Incident Response Frameworks
But what type of information is most useful to companies and their CSIRTs as actionable intelligence? And, even more fundamentally, what terminology can be used to characterize the complex conditions of a threat landscape? The first framework we look at seeks to address this issue.
Howard & Longstaff’s Taxonomy
A scientist at Sandia National Labs in Livermore, California (John Howard), and a colleague of his at the Computer Emergency Response Team, Coordinating Center (CERT-CC) (Thomas Longstaff) first started looking at the issue of a common language for communicating incident response information across organizations in 1998. They developed what became the most common framework, or taxonomy, to be used by information assurance professionals for about a decade. They advanced the notion that to share information there must be a valid system for classifying all of the factors present in an “incident” including: attackers, tools, access points, results, and objectives. They characterized this as taxonomy, defined as a system for classifying various phenomena across events. Figure 2 provides a simplified illustration of the Howard and Longstaff model.
Figure 2. Howard & Longstaff’s Incident Response Taxonomy

Adapted from Howard and Longstaff, 1998
Their interest was primarily focused on establishing a common language for use at the firm level, within an organization. It would be another five years before a viable framework came out for sharing.
AirCERT
By 2003 the idea of an Automated Incident Response (Air) capability had gained ground within the CERT-CC at the Software Engineering Institute at Carnegie Mellon (Trammel, 2005). Object oriented programming principles within a distributed computing architecture drove the design of the AirCERT. The need for participants in a sharing schema to maintain anonymity led to a three-part model that included: sanitizing the data, normalizing the data, and sharing the data. To accomplish this AirCERT architects used three different tools:
- Normalizers – to extract event logging data from devices on a network;
- Collectors – to collect and store these data in a format that could be used for analysis; and
- Publishers – to exchange data with other collectors.
The designers of AirCERT built the framework on commonly accepted protocols such as Simple Network Markup Language (SNML) a data representation model for transport control protocol (TCP), user datagram protocol (UDP) and Internet control message protocol (ICMP) network traffic. Although AirCERT is no longer in use, CERT continues to maintain the library of utilities developed under this framework for historical purposes (AirCERT, 2003).
The importance of this step in the evolution of sharing frameworks is that the design team specified XML as the preferred format for data exchange (Hollenbeck, 2003, January). The design goals for XML were simplicity, generality, and usability for data transfer between different applications and different transfer protocol over the Internet. Nested within AirCERT’s XML library definitions were other exchange formats, two of which are presented below.
IODEF/IDMEF
The Internet Engineering Task Force’s (IETF’s) Incident Object Description Exchange Format (IODEF) focused on the entire incident, not on individual events. The Incident Handling Working Group recognized that there was a need to convert a largely manual process by individual CSIRTs into an automated process (Gilbert, 2012, January 19). IODEF is also referenced as RFC 5070 (Danyliw, 2007, December). The IODEF provides good detail on incident flow and temporal data. And, it has a built-in capability for access control to limited portions of a report.
Developed in parallel to the IODEF was the Intrusion Detection Message Exchange Format (IDMEF). This effort was aimed at defining the data formats and exchange protocols that could be used by various automated intrusion detection systems. It had an ancillary use as a tool for rolling up these data for display in management consoles.
One widely used open source intrusion detection system using a management console is Prelude (Vandoorselaere, 2012). Another tool used for aggregating multiple intrusion detection feeds on computer networks is Snort (Roesch, 2010). The most popular tool for computer and network penetration testing, Metasploit, is also available as an open source tool (Rapid7, 2013). But apart from the internal monitoring of intrusions there was also a need for private sector companies to begin to work with public sector law enforcement agencies to begin to quantify the volume of attacks coming from state and non-state actors. That step came about through the next framework in the evolution of cybersecurity threat intelligence sharing.
Vocabulary for Event Recording and Incident Sharing (VERIS)
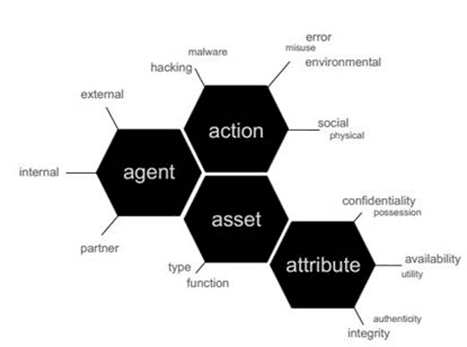
The Vocabulary for Event Recording and Incident Sharing Framework (VERIS) is a taxonomy aimed at standardizing the language used to characterize and categorize incident responses (Verizon RISK Team, 2010). It was developed as a way for law enforcement agencies from several countries around the world to share incident data as part of the Verizon RISK Team’s Data Breach Investigations Report (DBIR). It covers 14 different sectors and documents metrics on the incidents, as well as assets affected.
VERIS uses the Parkerian Hexad developed by Donn B. Parker rather than the traditional confidentiality, integrity, availability (CIA) triad (Gilbert, 2012, January 19). It is based on the A4 threat model (Agent, Action, Asset, and Attribute) (Verizon RISK Team, 2010) as discussed by Ginn (2013, August). Figure 3 illustrates the A4 threat model.
Figure 3. VERIS A4 Model
Adapted from Verizon RISK Team, 2010.
According to Appendix B of the 2013 DBIR Report there are now 19 contributors to the VERIS framework, including many CERTs around the world (Verizon RISK Team, 2013). The reader should note that the key distinguishing feature of the VERIS is that it is an ex post facto analysis that documents breaches after they have occurred. Due to the international size and scope of the studies, they can be useful to an analyst for gauging trends and patterns. However, CSIRTs need real-time threat intelligence and, therefore, must rely on other sources as well.
Open Indicators of Compromise (OpenIOC)
The Mandiant-sponsored open source indicators of compromise (OpenIOC) project is an example of a framework developed by a private company as a community resource for CSIRT operations. Like other open source tools, it is portable, extensible, and available for many different types of deployments. It is written in XML providing users with a lightweight tool that can easily be extended with simple utilities that meet a particular deployment.
Mandiant has detailed over 500 types of evidence that can be gathered over an enterprise. Using a layered architecture the tool combines static, signature-based matching with dynamic behavior-based matching (OpenIOC.org, 2011). It is accessed through the IOC Finder which is a free tool that can be downloaded from the Mandiant website. Its current version is Rev. 1.0 with a release date of October 31, 2011. It is supported on Windows XP, Windows Vista, and Windows 7 (32-bit and 64-bit). The reader will note that the scope of the OpenIOC is a subset of the original taxonomy envisioned by Howard and Longstaff. But beyond private sector initiatives offering open source community tools the U.S. government recognized the need for a vendor-neutral framework and brought together many of the features of previous sharing frameworks.
The MITRE Framework
Developed by MITRE under contract to the Department of Homeland Security (DHS) this framework has been adopted by the Financial Services Information Sharing and Analysis Center (FS-ISAC) for use as an information sharing framework (Struse, 2012). It is the most recent in the evolution of information sharing frameworks. Three of the frameworks for vulnerability characterization, the Open Vulnerability and Assessment Language (OVAL) (MITRE, 2013b), Malware Attribute Enumeration and Characterization, (MAEC) (MITRE, 2013c) and Common Attack Patterns Enumeration and Classification (CAPEC) (MITRE, 2013d) were discussed in Ginn (2013, August). This section focuses specifically on the tools most useful for incident response sharing.
STIX. There have been two key efforts developed by MITRE for the purpose of standardizing and normalizing information on threats. The first, Standardizing Cyber Threat Intelligence Information with the Structured Threat Information eXpression (STIX) (Barnum, 2012), establishes a unifying architecture for a diverse set of metrics, including:
- Cyber Observables
- Indicators
- Incidents
- Adversary Tactics, Techniques, and Procedures (including attack patterns, malware, exploits, kill chains, tools, infrastructure, targeting, etc.)
- Exploit Targets (e.g., vulnerabilities and weaknesses)
- Courses of Action (e.g., incident response or vulnerability/weakness remedies)
- Cyber Attack Campaigns
- Cyber Threat Actors
According to discussions with a representative on the FS-ISAC working group on STIX, the biggest impediment to widespread adoption of these frameworks is access control. In other discussions with a representative from a threat intelligence aggregator it was pointed out that companies want to receive threat information, but not share their own threat data, also impeding progress on STIX adoption.
The design of STIX involves four Use Cases. These are:
- Analyzing Cyber Threats
- Specifying Indicator Patterns for Cyber Threats
- Managing Cyber Threat Response Activities
- Sharing Cyber Threat Information
We are focused here primarily on the fourth Use Case: Sharing Cyber Threat Information. Figure 4 illustrates the four Use Cases.
Figure 4. STIX Core Use Cases

Source: Barnum et al., 2012.
TAXII. The second MITRE information sharing tool is a framework for automating the sharing of cyber observable eXpressions (CybOX) . It is called The Trusted Automated Exchange of Indicator Information (TAXII) (Connolly, 2012, November 8). It is a community-driven effort that seeks to extend the threat intelligence of CSIRTs beyond what is known internally through reconnaissance and digital forensics. It is for sharing of anonymized, robust, high-volume, automatic indicators of cyber activity in a common format that is product and organization agnostic. TAXII works in conjunction with STIX for automating the transfer of data. The reader will note that the NIST Security Content Automation Protocol (SCAP) standard was finalized at about the same time, chronologically, as the CybOX/STIX/TAXII triad. The purpose of SCAP is for product accreditation and can work in conjunction with the CybOX/STIX/TAXII triad.
Connolly et al. have modeled the attacker kill chain in their introduction to TAXII (2012, November 8). The early part of the attacker’s kill chain, represented by the recon, weaponize and deliver stages, as shown on Figure 5, are the moments of greatest opportunity for the CSIRT defenders. Here, with the right threat intelligence, they may be able to detect anomalous patterns in the network or on host machines. After the “exploit” event the attacker seeks to control, execute and maintain his foothold in the network.
Figure 5. Adaptation of Computer Defense Network Approach to IR
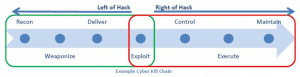
Source: Connelly et al. (2012).
The objective of a robust information sharing program is to obtain enough threat intelligence from trust partners within the sector that the exploit is circumvented during the “left of hack” stage. CSIRTs from small and medium-sized enterprises that participate in an information sharing program can gain an asymmetric advantage during this critical stage.
Table 1 summarizes, in chronological order, the key contributions that each of the six frameworks, discussed above, and has made to the field.
Table 1. Summary of Information Sharing Frameworks Covered
| Name | Year | Purpose | Model | Adopters | |||||
| Howard & Longstaff Taxonomy | 1998 | Developed a common language and method of classification for incident responders | 5-Part Model (Attackers, Tools, Access, Results, Objectives) | Private sector companies; academic information assurance | |||||
| AirCERT | 2005 | Extended the H&L taxonomy to a distributed model using XML. | Distributed computing | CERT; CSIRTs | |||||
| IETF Framework | |||||||||
| Incident Object Description Exchange Format (IODEF) | 2007 | Developed mechanism for detailed capture of incident flow. | RFC 5070 of Network Working Group | IETF Network Working Group & sponsors | |||||
| Intrusion Detection Message Exchange Format (IDMEF) | 2007 | Defined data formats and exchange protocols for automated intrusion detection programs and devices. | RFC 4765 of Network Working Group | IETF Network Working Group & sponsors | |||||
| Vocabulary for Event Recording and Incident Sharing (VERIS) | 2010 | Developed approach for sanitizing breach data from multiple international law enforcement agencies. | A4 Model (Agent, Asset, Action, Attribute) | Verizon, U.S. Secret Service + 18 international organizations | |||||
| Open Indicators of Compromise (OpenIOC) | 2011 | Defines over 500 static and dynamic patterns that can be used as evidence of a compromise. | Portable, extensible XML-based | Mandiant; open source community | |||||
| MITRE | |||||||||
| Cyber Observable eXpression (CybOX) | 2013 | A framework to capture and characterize events that are observable in the operational domain. | XML-based | Major investment brokerages and banks; many firms identified a part of critical infrastructure | |||||
| Structured Threat Information eXpression (STIX) | 2012 | Community-driven effort to define a common language for threat information. | Four Use Cases drive definition of each domain. | Major investment brokerages and banks; many firms identified a part of critical infrastructure | |||||
| Trusted Automatic Exchange of Indicator Information (TAXII) | 2012 | A portable, extensible framework for cross-community sharing of CybOX in a structured manner. | XML-based; Hub-and-Spoke deployment | Major investment brokerages and banks; many firms identified a part of critical infrastructure | |||||
Although this short history is not comprehensive, it gives you a flavor of the key issues that have been addressed to date for information sharing frameworks. Efforts to annonomyze data, provide interoperability, and encourage wide user community participation have been key. In my next essay I’ll present some of the incentives that are being discussed as part of the NIST Framework information sharing program to encourage wider participation on information sharing of intrusion and breach incidents.
_________________________________
References:
AirCERT, 2003, LibAirUtil, Pittsburg, PA, Computer Emergency Response Team [CERT] Coordinating Center.
Barnum, S., 2012, Standardizing Cyber Threat Intelligence Information with the Structured Threat Information eXpression (STIX™), MITRE.org.
Connolly, J., Davidson, M., Richard, M., Skorupka, C., 2012, November 8, The Trusted Automated eXchange of Indicator Information (TAXII™), MITRE.org.
Danyliw, A., Meijer, J., Demchenko, Y., 2007, December, RFC5070 – Incident Object Description Exchange Format, Internet Engineering Task Force [IETF], Network Working Group.
Debar, H., Curry, D., Feinstein, B., 2007, March, RFC4765: Intrusion Detection Message Exchange Format (IDMEF), The Internet Engineering Task Force [IETF] Trust.
Gilbert, K., 2012, January 19, A survey of computer incident information sharing frameworks, The Digital4rensics Blog.
Ginn, R. J., 2013, August, Sharing Cybersecurity Intelligence Within The Banking and Financial Services Sector: Northfield, VT, Norwich University.
Hollenbeck, S., Rose, M., Masinter, L., 2003, January, RFC3070 – Guidelines for the Use of Extensible Markup Language Within IETF Protocols.
Howard, J. D., 2009, Using a common language for computer security incident information, in S. Bosworth, Kabay, M.E., Whyne, E.,, ed., Computer Security Handbook (5th ed.): Hoboken, NJ, John Wiley & Sons, Inc.
Howard, J. D., Longstaff, T.A., 1998, A Common Language for Computer Security Incidents, Livermore, CA, Sandia National Labs.
MITRE, 2013b, Open Vulnerabilities Assessment Language (OVAL) Adoption.
MITRE, 2013c, Malware Attribute Enumeration and Characterization (MAEC).
MITRE, 2013d, Common Attack Pattern Enumeration and Classification (CAPEC).
National Institute of Standards and Technology [NIST], 2011, September, The technical specification for the security content automation protocol (SCAP): SCAP version 1.2, Gaithersburg, MD, U.S. Department of Commerce.
OpenIOC.org, 2011, Sophisticated Indicators for the Modern Threat Landscape: An Introduction to OpenIOC.
Rapid7, 2013, Metasploit.
Roesch, M., 2010, Snort, Snort.org.
Struse, R., Barnum, S., 2012, Trusted Automated Exchange of Indicator Information.
Trammel, B., Danyliw, R., Levy, S., Kompanek, A., 2005, AirCERT: The Definitive Guide.
Vandoorselaere, Y., 2012, Prelude, a CS Product.
Verizon RISK Team, 2010, Verizon Enterprise Risk and Incident Sharing Metrics Framework.
Verizon RISK Team, 2013, Data Breach Investigations Report., New York, NY, Verizon.